Course Introduction
Professional certification
Google Professional Security Operations Engineer
Detect, investigate, and respond to threats on Google Cloud and hybrid environments. This guide centers on detections, playbooks, and exam-ready SOC practices.
Want to pass faster?
Get practice tests + the latest deals/discount codes
Get the latest from Cloud-Edify
Get two free courses coupons. Curated learning content, tools, and deal alerts—straight to your inbox.
Detect
Use Chronicle/SCC findings, logging, and threat intel to build effective detections.
Investigate
Hunt with logs, correlate alerts, and validate scope with repeatable steps.
Respond
Automate containment and remediation with playbooks, SOAR, and least-privilege controls.
Status
Interactive guide is live; more labs and flashcards are coming.
SecOps Platform + Threat Response
Use Google Security Operations, SCC, and GTI to detect, investigate, and respond to threats across cloud and hybrid environments.
Exam Overview
Length: 2 hours
Format: 50-60 multiple choice and multiple select questions
Key platforms: Google Security Operations, Security Command Center, Google Threat Intelligence
Focus: detections, investigations, SOAR automation, and incident response
Exam Domains (6 Sections)
Open each section for key objectives.
1) Platform operations (14%)
Architecture & integrations: SCC, Cloud IDS, and third-party feeds.
Access control: RBAC, IAM, workforce identity federation, and API keys.
2) Data management (14%)
Ingestion & parsing: forwarders, UDM mapping, parser extensions.
Context & enrichment: entity graph and UDM fields like principal.ip and target.ip.
3) Threat hunting (19%)
YARA-L: rule language for detections and correlation.
Retrohunt: search historical data with GTI indicators.
4) Detection engineering (22%)
Rules: single-event vs multi-event and reference lists for tuning.
Risk scoring: prioritize alerts with risk analytics and reduce false positives.
5) Incident response (21%)
Investigations: asset view timelines and SCC context.
SOAR playbooks: automate containment and integrate third-party actions.
Case management: triage to remediation with SLA tracking.
6) Observability (10%)
Dashboards: Looker widgets and BigQuery reporting.
Health: silent source detection and EPS monitoring.
How to Use This Guide
- Mark off topics as you master them.
- Answer self-check questions after each section.
- Practice mini scenario challenges to apply concepts.
Cheatsheet: Key Terminology
| Term | Definition |
|---|---|
| UDM | Unified Data Model for normalized logs. |
| YARA-L | Detection language for UDM-based rules. |
| GTI | Google Threat Intelligence feeds and enrichment. |
| SCC | Security Command Center posture and threat tool. |
| SOAR | Orchestration and automation for response playbooks. |
| Parser | Script mapping raw logs into UDM fields. |
| Retrohunt | Search historical logs for new indicators. |
Flashcards
SecOps concepts, tools, and detection patterns
Question Text
Click to reveal answerAnswer Text
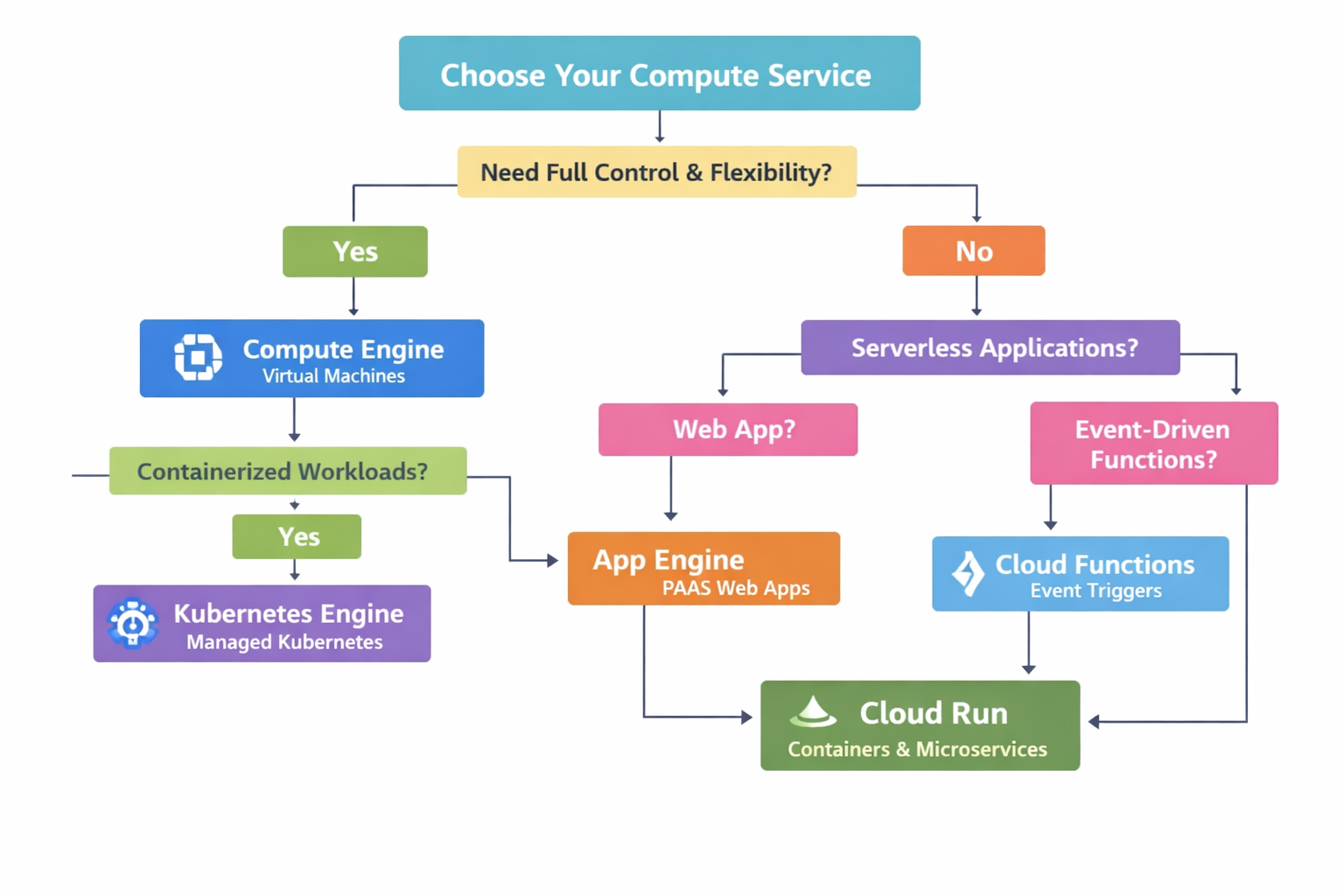
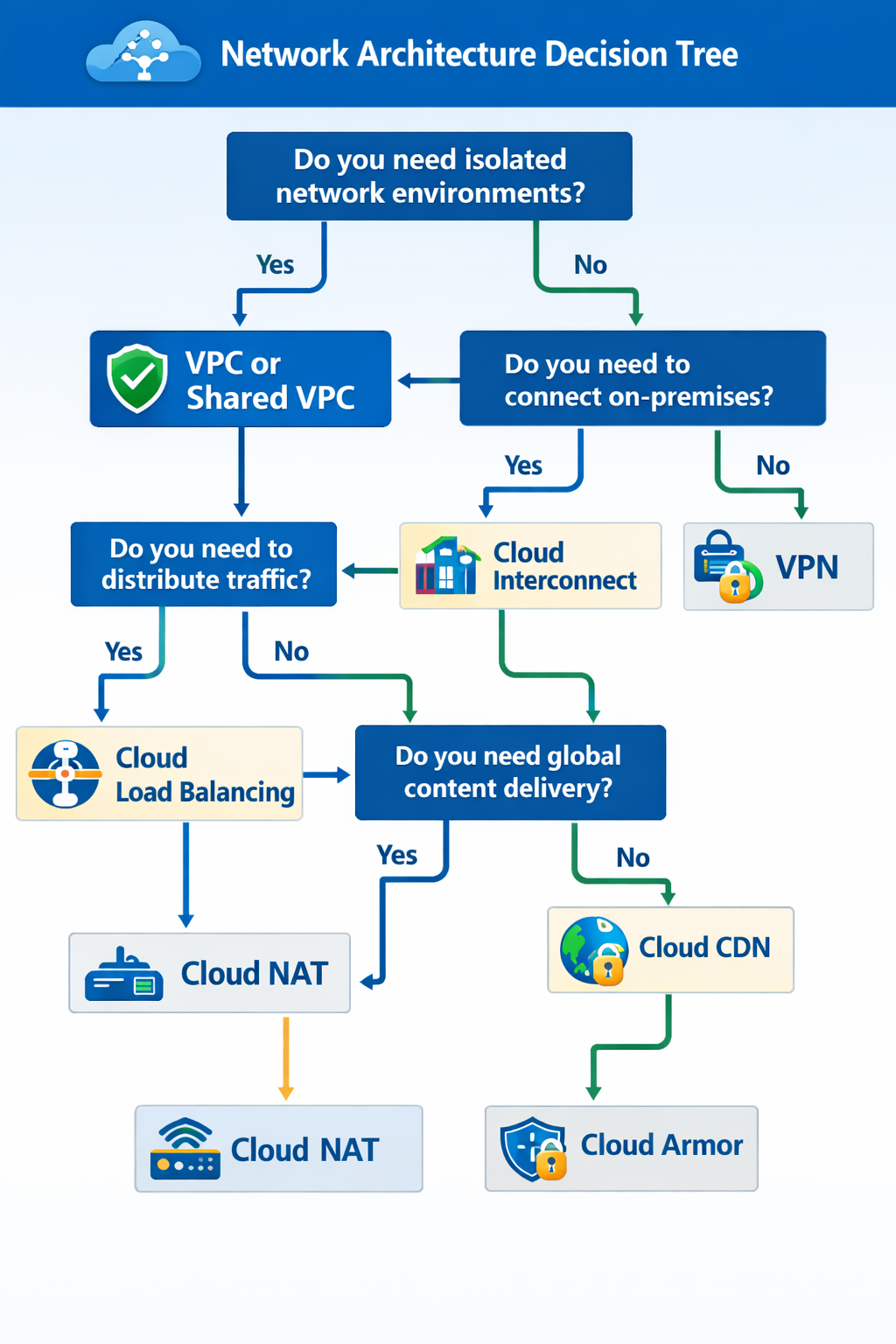
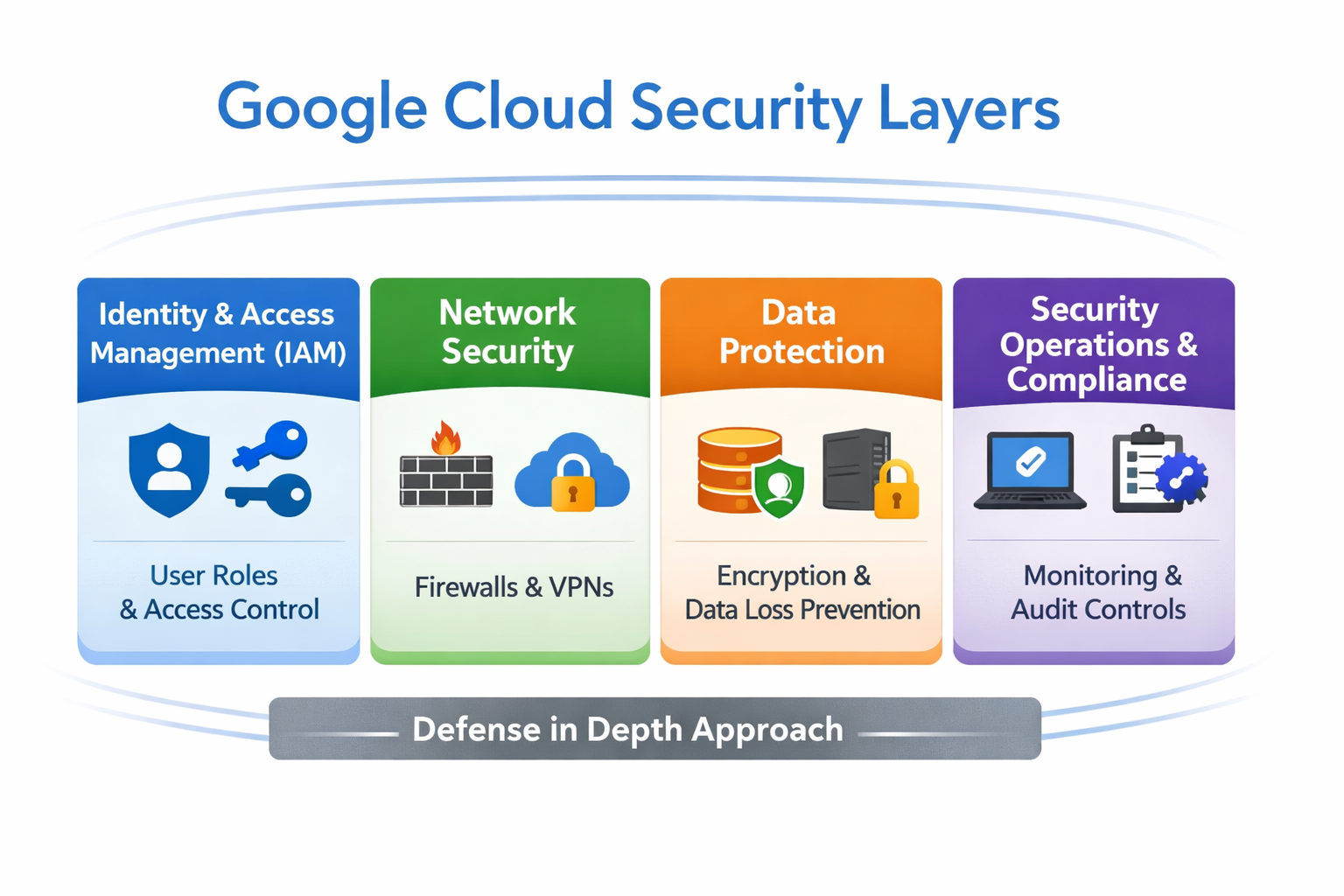
SecOps Decision Diagrams
Click a title to show/hide diagrams. Click images to expand.